Technology
Who Called Me UK: Unmasking Unknown Numbers
Published
9 months agoon
By
Ninja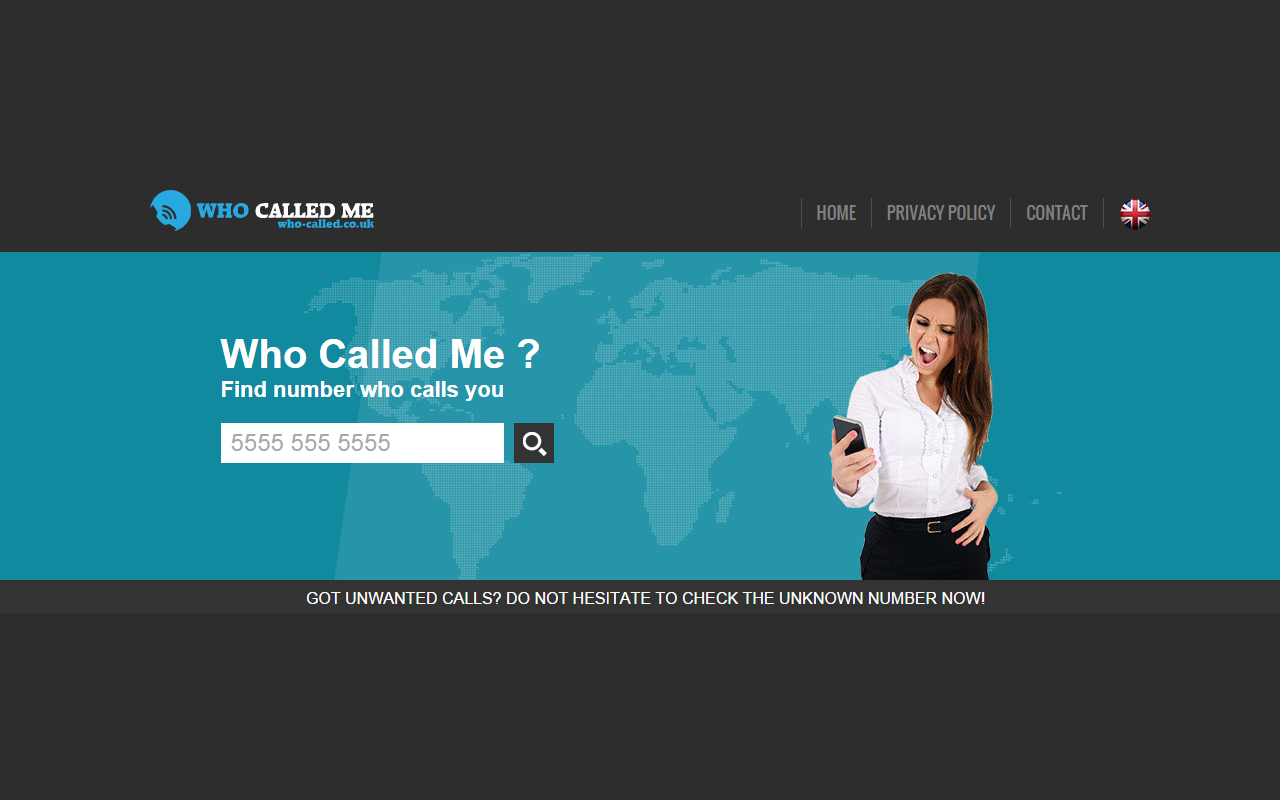
Have you ever received a call from an unknown number and felt that familiar pang of curiosity or anxiety? You’re not alone. Many people in the UK find themselves pondering, “Who called me UK?” The rise of telemarketing, scams, and unrecognized numbers can leave anyone feeling uneasy. Thankfully, tools like Truecaller have emerged to help us navigate this world of mystery calls. Whether you’re trying to track down a missed call or simply want peace of mind about who’s on the other end, understanding reverse phone lookup services is essential. Let’s dive into how these technologies work and discover ways to reclaim your communication with confidence!
Who Called Me UK: Unmasking Unknown Numbers
In today’s digital age, unknown numbers can often signal annoyance or even danger. The question “Who called me UK?” is more than just casual curiosity; it’s a necessity for safeguarding your personal space. With unsolicited calls on the rise, unmasking these mystery callers has become crucial.
Many individuals feel vulnerable when their phones ring with unfamiliar numbers. Fortunately, technology offers solutions to identify and block unwanted calls. By utilizing reliable phone number lookup tools, you can reclaim control over your communication and reduce the stress of dealing with irritating interruptions.
Why Use Truecaller For Phone Number Lookup
Truecaller is a powerful tool for anyone looking to identify unknown numbers. With its vast database, it can quickly reveal the identity of callers that might otherwise remain a mystery. This functionality helps users avoid unwanted spam and scams, making communication safer.
Using Truecaller also enhances your peace of mind. Whether it’s an unexpected call from an unfamiliar number or just curiosity about who’s trying to reach you, this app provides instant answers. Users benefit from community-driven insights, ensuring they stay informed and secure in their phone interactions.
Trust your communication with Truecaller
Truecaller enhances your communication experience by ensuring you know exactly who you’re talking to. With its vast database, it identifies unknown numbers and helps filter out spam calls effectively. You can trust that the app uses community-driven data for accurate results.
Moreover, Truecaller prioritizes user safety and privacy. By providing real-time information about incoming calls, it empowers users to make informed decisions before answering. This peace of mind allows you to engage in conversations without the fear of unwanted interruptions or scams lurking on the other end of the line.
Understanding Reverse Phone Lookup
Reverse phone lookup is a powerful tool for identifying unknown callers. By entering a phone number, users can access information about the caller, such as their name and address. This process helps people make informed decisions before answering calls.
The service works by leveraging databases that compile public records and user-generated data. It’s particularly useful in combatting spam or scam calls, allowing individuals to avoid unwanted communication. Understanding how reverse phone lookup functions gives you greater control over your interactions and enhances your security in today’s digital world.
How Truecaller’s Phone Number Search Works
Truecaller’s phone number search operates on a vast database of user-generated contacts. When someone calls you, the app identifies the number by cross-referencing it with its extensive records. This instant lookup provides real-time information about unknown callers.
When users receive calls from unidentified numbers, Truecaller displays relevant details like names and locations based on community contributions. The more people use Truecaller, the smarter it becomes at recognizing and labeling incoming calls accurately, making it an essential tool for anyone wanting to identify who called them in the UK.
Making the Most of Phone Number Search Services
Phone number search services can be powerful tools for anyone looking to identify unknown callers. By using these platforms effectively, you can quickly determine the source of calls that disrupt your day. Start by entering the full phone number in the search bar, ensuring accuracy for better results.
Additionally, leverage user reviews and community feedback on these apps. This will help you gauge the reliability of information provided. The more informed you are about potential scammers or telemarketers, the safer your communication becomes. Embrace technology to stay connected without fear!
Key Features of Truecaller’s Reverse Phone Lookup
Truecaller’s Reverse Phone Lookup boasts several key features that enhance user experience. At its core is an extensive database, allowing you to identify unknown callers quickly. The app taps into millions of users globally, making it a powerful tool for uncovering anonymous numbers.
Additionally, Truecaller provides real-time spam detection and blocking. This means unwanted calls are filtered out before they even reach you. With caller ID functionality integrated seamlessly, every call becomes transparent, ensuring better communication management and peace of mind for users throughout the UK.
Ensuring Security and Reliability
When using phone number lookup services, security is paramount. You want a platform that safeguards your personal information while providing accurate data about unknown callers. Truecaller stands out by employing encryption and strict privacy policies to ensure user safety.
Reliability also plays a critical role in these tools. A trustworthy service should consistently deliver correct caller details without compromising speed or efficiency. Truecaller’s extensive database and community-driven approach enhance its reliability, empowering users to confidently identify numbers they don’t recognize, all while feeling secure in their online interactions.
Exploring International Number Searches
Exploring international number searches can open up a world of possibilities. Whether you’re traveling abroad, conducting business internationally, or reconnecting with old friends, knowing who’s on the other end of the line is crucial.
Various apps and services offer global phone number lookup features that cater to these needs. With just a few taps, you can identify callers from different countries, ensuring your conversations are trustworthy and informed. This capability makes it easier to navigate communication in our increasingly interconnected world.
Comparing Reverse Phone Lookup Tools
When it comes to reverse phone lookup tools, options abound. Each platform offers unique features that cater to different user needs. Some focus on speed and accuracy, while others prioritize extensive databases or user-friendly interfaces.
Truecaller stands out for its vast community-driven database, while Wotcha excels in privacy features. Sync.
ME provides instant identification through social media integration. Assessing which tool fits your lifestyle can enhance your experience in uncovering unknown callers effectively. Exploring these differences helps you make an informed choice tailored to your preferences and requirements.
Overview of Wotcha: Who Called Me?
Wotcha is a popular tool for identifying unknown callers in the UK. It provides users with a straightforward interface, making it easy to search for and track down mysterious numbers. With its growing database, Wotcha helps you avoid unwanted calls from telemarketers and potential scams.
The app allows users to report unwanted calls, contributing valuable information back into the community. This collective effort enhances accuracy over time, ensuring that you’re better informed about who’s on the other end of the line before picking up your phone.
Data Safety in Phone Number Lookup Apps
Data safety is a significant concern with phone number lookup apps. Users often share their personal information, which can be vulnerable to breaches or misuse. It’s crucial to choose platforms that prioritize user privacy and implement robust security measures.
Many reputable services employ encryption protocols and strict data protection policies. Always read the terms of service and privacy policy before using an app. This helps ensure your information remains secure while you search for unknown callers, providing peace of mind in an increasingly connected world.
Support and Similar Apps
When navigating the world of unknown calls, having reliable support is crucial. Numerous apps complement Truecaller and Sync.
ME in helping users identify callers. Options like Whoscall and CallApp provide similar features, making it easier to uncover hidden numbers.
Each app comes with unique functionalities tailored to enhance user experience. Some focus on community-driven databases while others prioritize speed or additional security measures. Exploring these alternatives can help you find the right solution that fits your needs best when tackling mystery calls effectively.
Unveiling Caller Identity
Identifying unknown callers can be frustrating. With so many spam numbers and unsolicited calls, knowing who’s on the other end is essential for peace of mind. By using advanced technology, apps like Truecaller help unveil caller identities swiftly.
These tools leverage vast databases to match numbers with names or businesses, transforming your phone into a powerful detective. The convenience of having this information at your fingertips allows you to make informed decisions about answering calls or blocking unwanted ones, ensuring that your communication remains secure and reliable.
Essential Features of Sync.
ME
Sync.
ME is designed to simplify the way you manage calls. With its innovative spam detection feature, it identifies unwanted numbers in real time, ensuring your phone stays free from irritating telemarketers. Users benefit from seamless integration with their contacts, enhancing your calling experience.
Another standout feature is its social media linking capability. Sync.
ME pulls in information from various platforms and updates contact details automatically. This keeps your connections current without extra effort on your part, making it a handy tool for both personal and professional communications alike.
Instant Identification with Sync.
ME App
The Sync.
ME app stands out by offering instant identification for unknown numbers. With its extensive database, it provides real-time information about incoming calls. Users can quickly discover who’s on the other end of the line without any hassle.
Sync.
ME is designed to be user-friendly and efficient. Its intuitive interface allows you to search for numbers seamlessly, making it a go-to choice for many. Whether you’re dealing with an annoying telemarketer or trying to reconnect with an old friend, this app has you covered.
You may like
Technology
SSIS 46: An Overview of SQL Server Integration Services Version 46
Published
2 months agoon
January 3, 2026By
Ninja
Introduction
SQL Server Integration SSIS 46 Services (SSIS 46) is a powerful data integration tool provided by Microsoft, part of the SQL Server suite, that helps manage data extraction, transformation, and loading (ETL). SSIS is primarily used for data migration, transformation, and workflow automation. Version 46 (SSIS 46), though a less publicized release compared to major version jumps, continues to build upon its predecessors’ capabilities to offer even more flexibility, scalability, and performance improvements for modern data integration needs.
In this article, we’ll explore the key features, improvements, and use cases of SSIS 46, providing insights into how it can improve enterprise data workflows and enhance data integration tasks.
What is SSIS?
SSIS is a platform for data integration and transformation that allows businesses to automate the data movement between different systems. It can extract data from various sources like databases, flat files, XML files, and web services. Once data is extracted, it can be transformed by applying business rules, data cleansing, or other modifications. Finally, it loads the transformed data into destination systems such as databases, data warehouses, or other applications.
SSIS is widely used for tasks like:
- Migrating data between systems
- Data cleansing and standardization
- Building data warehouses and ETL pipelines
- Automating database maintenance
- Integrating data from heterogeneous sources
With each version, SSIS improves performance, adds new features, and refines existing functionalities to make the tool more versatile in handling complex data integration scenarios.
Key Features and Improvements in SSIS 46
SSIS 46 introduces a number of enhancements and features designed to address modern data integration challenges. Some of the major highlights include:
1. Performance Enhancements
- Optimized Data Flow Engine: SSIS 46 brings significant performance improvements to the data flow engine. The enhancements make SSIS faster and more efficient when handling large datasets, minimizing execution time for common ETL processes. This is especially crucial for organizations dealing with big data or real-time data streaming.
- Parallel Execution: More advanced options for parallel execution of tasks have been introduced in SSIS 46. This allows for better scalability, as multiple tasks or data flows can run simultaneously, reducing overall processing time.
2. Enhanced Data Transformation Capabilities
- Built-In Transformations: SSIS 46 comes with enhanced built-in transformations such as Lookup, Merge Join, and Aggregate transformations, which are optimized for modern data architectures. These improvements allow data professionals to create complex transformation logic without sacrificing performance.
- New Transformation Types: SSIS 46 introduces new transformation types to support specific use cases. For instance, there are more robust capabilities for working with JSON data, making it easier to manipulate unstructured or semi-structured data.
3. Improved Debugging and Monitoring Tools
- Advanced Debugging: Debugging ETL processes in SSIS can be challenging when the workflow becomes complex. In SSIS 46, debugging capabilities have been enhanced, providing better step-through debugging, breakpoints, and more detailed logging to trace errors in data flows or control flows.
- Real-Time Monitoring: The improved monitoring tools allow data integration tasks to be tracked in real time, giving administrators and developers better visibility into ongoing workflows. This is crucial for large-scale deployments where proactive error detection and performance monitoring are vital.
4. Support for Cloud-Based Integration
- Azure Integration: With the growing demand for cloud data processing, SSIS 46 has improved integration with Microsoft Azure. It supports seamless integration with Azure Data Lake, Azure SQL Database, and Azure Synapse Analytics, making it easier for businesses to move data between on-premises systems and cloud platforms.
- Hybrid Scenarios: SSIS 46 also enhances hybrid data integration scenarios, where data resides both in the cloud and on-premises. These features enable more flexible architectures, ensuring smooth ETL operations across different environments.
5. Security Enhancements
- Enhanced Data Protection: SSIS 46 introduces better security measures for handling sensitive data. It supports more robust encryption methods and offers improved authentication and authorization features to ensure that data is securely transferred between systems.
- Improved Integration with Active Directory: SSIS 46 integrates more efficiently with Active Directory, which simplifies user management and permissions for SSIS packages across an enterprise environment.
6. Support for Modern Data Formats
- JSON and XML Processing: SSIS 46 offers enhanced support for processing JSON and XML data, which is increasingly common in modern data ecosystems. The new features enable seamless parsing, transformation, and loading of data in these formats.
- Parquet and Avro: With SSIS 46, integration with modern data formats like Parquet and Avro has been improved. These formats are commonly used in big data environments and are well-suited for large-scale data processing.
7. Increased Integration with Third-Party Tools
- Third-Party Connector Support: SSIS 46 includes extended support for third-party connectors, allowing businesses to integrate with a broader range of applications, databases, and services. This helps organizations leverage SSIS in diverse environments and across various platforms.
- Marketplace Add-ons: SSIS 46 opens up better integration with the Microsoft marketplace for third-party add-ons and custom tasks, giving users even more flexibility to extend the functionality of SSIS.
Use Cases for SSIS 46
Given its flexibility and wide array of features, SSIS 46 can be employed across numerous scenarios, including:
1. Data Warehouse Development
SSIS is commonly used to populate data warehouses by extracting data from source systems, transforming it (e.g., cleansing, standardizing), and loading it into a structured format in a data warehouse. With the performance improvements and better cloud integration in SSIS 46, businesses can efficiently handle both on-premises and cloud-based data sources.
2. Business Intelligence (BI) Workflows
SSIS 46 supports BI workflows by facilitating data integration from multiple sources and ensuring data is ready for analytics. For instance, a business intelligence team might use SSIS to consolidate transactional data from multiple databases, transform it into a reporting format, and load it into a BI platform like Power BI or SQL Server Analysis Services (SSAS).
3. Real-Time Data Integration
In industries such as finance or e-commerce, real-time data integration is critical. SSIS 46 enables near real-time data processing by integrating with streaming data sources like Azure Event Hubs or Kafka, ensuring that business decisions are based on the most current data available.
4. ETL Pipelines in Big Data Environments
Organizations working with big data, such as in retail, manufacturing, or healthcare, require scalable ETL solutions. With SSIS 46’s support for big data formats like Parquet and its cloud integration capabilities, businesses can efficiently manage large datasets and integrate them with their existing systems.
Conclusion
SSIS 46 builds upon the already powerful foundation of previous SSIS versions, making data integration processes faster, more secure, and more flexible. With its cloud integration capabilities, enhanced performance, and support for modern data formats, SSIS 46 is a robust tool that can meet the needs of today’s data-driven organizations.
Whether you are managing a traditional data warehouse, integrating cloud-based data sources, or building complex ETL pipelines, SSIS 46 offers the tools and capabilities needed to handle the challenges of modern data integration and transformation. Its combination of performance improvements, security features, and expanded connectivity ensures that businesses can build scalable, secure, and high-performance data workflows with ease.
For organizations already using SSIS, upgrading to version 46 is highly recommended to take advantage of its improved features and performance. For new users, SSIS 46 provides a comprehensive and reliable solution for handling all types of data integration tasks.
Technology
MyPasokey: A Revolutionary Key to Seamless Online Security
Published
2 months agoon
January 1, 2026By
Ninja
In today’s digital age, safeguarding MyPasokey personal information is more critical than ever. From financial details to personal messages, the internet is a treasure trove of sensitive data that needs protection. This is where advanced authentication systems come into play. One such system, which has been gaining attention for its simplicity and security, is MyPasokey. But what is MyPasokey, and how does it work to ensure a safer online experience? This article will delve into MyPasokey, its features, and its potential impact on online security.
What is MyPasokey?
MyPasokey is a modern, cutting-edge authentication system designed to replace traditional passwords and improve online security for individuals and organizations alike. Built on the principles of strong encryption and user-friendliness, MyPasokey is a passwordless authentication solution that uses multi-factor authentication (MFA) to grant users access to online platforms securely.
Unlike traditional login methods, which require users to remember and input complex passwords, MyPasokey offers a more seamless experience. It eliminates the need for passwords entirely by using unique, dynamic access keys that are tied to the user’s device, ensuring that unauthorized individuals cannot gain access to your accounts even if they have your username.
The Problem with Passwords
To understand why MyPasokey is an essential development in the world of online security, we first need to examine the issues associated with traditional passwords. Passwords, while once considered a reliable method of securing online accounts, have shown significant vulnerabilities over the years:
- Weak Passwords: Many users continue to rely on weak or easy-to-guess passwords, such as “123456” or “password123.” Despite recommendations to use complex, randomized passwords, human behavior often defaults to convenience over security.
- Reused Passwords: People often reuse the same password across multiple platforms. If one platform is breached, attackers can exploit this reuse and gain access to numerous accounts.
- Phishing: Attackers often trick users into revealing their passwords through phishing schemes, where they impersonate trusted entities like banks or social media platforms.
- Data Breaches: Even with strong passwords, data breaches are a frequent occurrence. When an organization’s database is compromised, user credentials—often stored in plaintext or weakly encrypted formats—can be exposed, putting millions of people at risk.
- Password Management: Remembering and managing dozens of unique passwords can be cumbersome. Many users resort to password managers, but these too can be targets for cybercriminals.
These problems have led to the development of more robust authentication solutions like MyPasokey, which aims to eliminate the vulnerabilities associated with traditional passwords.
How MyPasokey Works
MyPasokey utilizes a passwordless authentication model, which is primarily based on cryptographic keys. The process involves a combination of a public key and a private key, where the private key is securely stored on the user’s device, and the public key is stored on the online service.
Here’s how MyPasokey functions:
- Enrollment: When you first set up your MyPasokey account, you will associate it with your device, typically a smartphone, tablet, or computer. The system generates a public-private key pair. The private key is stored securely on your device, while the public key is stored on the service’s server (the website or app you are trying to access).
- Authentication: When you want to log in to a service, the service sends a challenge to your device, which includes a nonce (a random number) to ensure that the request is legitimate. The device then uses the private key to sign the challenge, proving its identity.
- Verification: The signed challenge is sent back to the service, which uses the corresponding public key to verify that the response was generated by the correct device. If the challenge is verified successfully, access is granted to the user.
- No Passwords: The key takeaway is that this process does not involve the transmission or storage of passwords. Since no sensitive data like passwords are transmitted over the internet, the risk of interception is significantly reduced.
Additionally, MyPasokey can be integrated with multi-factor authentication (MFA). For example, after successfully logging in using the key, the system might ask for an additional form of authentication, like a fingerprint scan or a face recognition check, further enhancing security.
The Benefits of MyPasokey
- Enhanced Security: One of the most significant advantages of MyPasokey is its strong security. Since passwords are no longer involved, the risk of password theft, phishing, and brute force attacks is minimized. The use of cryptographic keys and MFA ensures that even if someone gains access to your device, they cannot easily access your accounts.
- Convenience: MyPasokey eliminates the hassle of remembering multiple passwords. With a single device and a secure authentication process, users can access their accounts quickly and without the need to enter passwords manually.
- Protection Against Data Breaches: Because MyPasokey relies on cryptographic keys instead of passwords, even in the event of a data breach, attackers cannot use stolen data to compromise users’ accounts. The key pair is unique and never exposed during the authentication process.
- Phishing Resistance: Traditional phishing attacks often rely on tricking users into providing their passwords. With MyPasokey, even if attackers manage to deceive users, they cannot steal a password because it is not used in the process.
- Fewer Password Management Issues: Forgetting passwords and having to reset them frequently can be a frustrating experience. MyPasokey resolves this issue by removing the need for passwords altogether.
- Better User Experience: For individuals and organizations alike, the simplicity of MyPasokey enhances the overall user experience. Users no longer need to juggle multiple passwords, and administrators can streamline security without compromising on protection.
Potential Applications of MyPasokey
MyPasokey is not limited to personal accounts. Its flexibility and security make it an ideal solution for a wide range of applications:
- Financial Institutions: Online banking and financial services can implement MyPasokey to protect user accounts from unauthorized access, reducing the risk of fraud and data theft.
- Enterprise Systems: Businesses can deploy MyPasokey for employees to access internal systems securely. The ease of use and MFA options make it a great choice for organizations seeking both security and efficiency.
- Social Media: As social media platforms continue to become prime targets for hackers, implementing MyPasokey can help protect users from account takeovers and data breaches.
- Healthcare: MyPasokey can be used to secure healthcare applications and systems, ensuring that sensitive medical data remains protected.
Challenges and Considerations
While MyPasokey offers numerous advantages, it is not without challenges. Some of the potential hurdles include:
- Adoption: Widespread adoption of passwordless authentication requires buy-in from both users and service providers. The transition from traditional password-based systems to MyPasokey may take time.
- Device Dependency: Since MyPasokey relies on the user’s device for authentication, losing the device or experiencing a hardware failure could lock the user out of their accounts. Backup authentication methods and recovery options need to be in place.
- Privacy Concerns: Some users may be wary of relying on a single authentication device for all their online accounts, especially if they are concerned about privacy and data collection practices.
Conclusion
In conclusion, MyPasokey represents a significant step forward in the evolution of online security. By eliminating the need for passwords and introducing a more robust authentication method, it addresses many of the vulnerabilities that have plagued traditional password-based systems. As the digital landscape continues to evolve, technologies like MyPasokey will play a crucial role in safeguarding our personal and professional lives from cyber threats. With its combination of security, convenience, and ease of use, MyPasokey could very well be the key to a safer online experience.
Technology
WhatsonTech: A Comprehensive Look at the Tech Media Platform
Published
2 months agoon
December 29, 2025By
Ninja
In today’s fast-evolving WhatsonTech tech landscape, staying up-to-date with the latest trends, reviews, and industry shifts is vital for tech enthusiasts, professionals, and consumers alike. One of the platforms that have gained significant attention in the world of technology media is WhatsonTech. WhatsonTech provides a range of content focused on the most recent developments in the tech world, offering insightful articles, reviews, product analyses, and features that cater to both tech enthusiasts and those seeking to understand how technology shapes their lives.
Introduction to WhatsonTech
WhatsonTech is a digital media platform that seeks to provide high-quality content on a wide variety of tech-related topics. Launched as a resource for tech lovers and professionals alike, it combines engaging and accessible content with deep insights into the world of tech. WhatsonTech covers an array of categories, such as product reviews, industry news, software updates, tech innovation, and gaming.
The platform’s mission is to create a reliable resource where users can find up-to-date information, in-depth guides, tutorials, and honest product assessments. Whether you’re a casual consumer looking for the best phone, a gamer trying to find your next gaming rig, or a tech professional trying to stay ahead of the curve, WhatsonTech aims to provide valuable insights for every reader.
Key Features and Content Categories
WhatsonTech organizes its content into several key categories, each aimed at serving a different segment of its audience. Here’s an overview of the major sections that define the platform:
1. Product Reviews
One of the core features of WhatsonTech is its product review section. The platform prides itself on delivering unbiased and thorough reviews of the latest gadgets, hardware, and software. From the newest smartphones, laptops, and tablets to smartwatches, headphones, and gaming consoles, WhatsonTech covers it all.
The reviews go beyond just surface-level impressions. They include performance analysis, battery life tests, design critiques, ease of use assessments, and comparison articles that pit different devices against each other. This detailed and critical approach helps users make informed purchasing decisions based on their needs and preferences.
2. Tech News and Industry Updates
Another vital area of WhatsonTech is its news section, which provides users with the latest updates on tech industry trends, mergers and acquisitions, breakthroughs in innovation, and product announcements. The platform keeps its readers informed about all the critical events happening in the world of technology.
Whether it’s a new Apple launch, a Google acquisition, or the latest AI breakthrough, WhatsonTech ensures that its audience has access to the most relevant and up-to-date information. The news articles are concise yet packed with facts and context, allowing readers to stay in the know without feeling overwhelmed by jargon.
3. Software and App Reviews
In the realm of software, WhatsonTech regularly reviews the latest apps and software tools across various operating systems, including Windows, macOS, Android, and iOS. Whether it’s new productivity tools, security software, or design applications, WhatsonTech tests the functionality, ease of use, and overall performance of software programs, providing helpful reviews and recommendations for users.
The platform also covers topics like software updates and patches, ensuring readers are always aware of any important changes to their operating systems and the applications they use daily. This is especially useful for those who want to ensure their software is up-to-date, secure, and running smoothly.
4. Gaming
With the gaming industry constantly growing, WhatsonTech has dedicated a section of its platform to everything related to gaming technology. From detailed hardware reviews of gaming laptops, desktops, and accessories to game reviews, industry events, and esports coverage, the platform is a go-to source for gamers of all types.
WhatsonTech not only reviews the latest game releases but also looks at gaming trends, offering guides on building custom gaming rigs, optimizing performance, and enhancing gameplay. The gaming section also covers virtual reality (VR) and augmented reality (AR) gaming, which are rapidly becoming popular as more immersive gaming experiences gain traction.
5. Guides and Tutorials
WhatsonTech provides comprehensive guides and tutorials that aim to educate users and make technology more accessible. Whether it’s a beginner’s guide to understanding the basics of cloud computing, a how-to on setting up a smart home, or an advanced tutorial on coding or network security, the platform strives to empower users with knowledge.
These tutorials are often written in a way that makes even complex concepts understandable for newcomers. For example, a step-by-step guide on how to troubleshoot common tech issues can help someone resolve problems independently, avoiding unnecessary tech support calls or repair costs.
The Importance of WhatsonTech in Today’s Tech Landscape
WhatsonTech stands out in a crowded tech media space by focusing on authenticity and accessibility. With so much information available online, finding reliable and accurate sources can be challenging. WhatsonTech sets itself apart by offering balanced opinions, clear assessments, and thoroughly researched articles.
For consumers, WhatsonTech is an essential resource for making well-informed decisions. Whether purchasing the latest smartphone or upgrading their home entertainment system, tech-savvy individuals know they can trust WhatsonTech’s product reviews to give them a comprehensive understanding of their options.
For industry professionals, WhatsonTech serves as an excellent platform for staying updated on market trends and technological advancements. The tech world moves at an incredibly fast pace, and WhatsonTech ensures that both casual tech enthusiasts and professionals can stay ahead by providing timely and relevant industry news.
Moreover, WhatsonTech’s ability to break down complex technological concepts into simple, digestible articles makes it a valuable educational resource for students, tech enthusiasts, and anyone looking to expand their knowledge of the digital world. This focus on clarity and simplicity allows WhatsonTech to connect with a diverse audience ranging from novices to experts.
What Makes WhatsonTech Stand Out?
- Unbiased Reviews: Unlike many other tech media platforms that are often influenced by sponsorships or affiliate marketing, WhatsonTech emphasizes objectivity in its product reviews. Each product is evaluated based on its own merits, and the pros and cons are clearly outlined.
- Engaging Content: WhatsonTech doesn’t just produce written content; it also integrates interactive features such as video reviews, unboxing content, and podcasts. These different formats help cater to a wider audience and keep the content engaging and dynamic.
- Focus on Innovation: The platform keeps a sharp eye on emerging technologies. Coverage of new innovations such as AI, 5G, blockchain, and quantum computing ensures that WhatsonTech readers are always at the forefront of the latest trends in tech.
- Community Engagement: WhatsonTech encourages interaction with its readers by allowing comments on articles and featuring discussions on social media platforms. This engagement builds a sense of community and allows users to share their experiences and opinions.
Conclusion
In a world where technology is an integral part of daily life, staying informed is essential. WhatsonTech has successfully carved a niche for itself in the tech media landscape by offering a balanced, informative, and user-friendly platform. Whether you’re looking for the latest gadget review, need a tutorial on how to fix a tech issue, or want to understand the latest in software and gaming, WhatsonTech is a trusted resource for all things tech.
As technology continues to evolve, WhatsonTech promises to remain a reliable source for news, reviews, and educational content. Its dedication to providing accurate and well-researched content ensures that it will continue to be a valuable asset for tech enthusiasts and professionals for years to come.
Trending
-

 Blog9 months ago
Blog9 months agoAbraham Quiros Villalba: Complete Information
-

 Technology5 months ago
Technology5 months agoLinki: Unveiling the Digital Connector in the Modern Age
-

 Entertainment9 months ago
Entertainment9 months agoهنتاوي.com: Your Gateway to Arabic-Subtitled Anime
-

 News9 months ago
News9 months agoDGMNews.com: A Comprehensive Overview of the Emerging Digital News Platform
-

 News7 months ago
News7 months agoClassroom‑60X: Unlocking the Future of Smarter Learning
-

 Blog9 months ago
Blog9 months agoSimpcitt: A New-Age Urban Marvel or a Digital Mirage?
-

 Blog9 months ago
Blog9 months agoThe Historical and Cultural Significance of Tonghou: A Journey Through Time
-

 Blog9 months ago
Blog9 months agoUnveiling The Life And Journey Of Keilani Bautista
